S3cmd : AWS command used to copy/Sync content to S3 bucket
s3cmd can be installed from epel repo or by manually compiling the code.
While installing from epel there could be dependency issue for the python.
while using epel repo we need the python version 2.4 in the server if you are having another version of python its better to go with the manual installation.
## RHEL/CentOS 6 32-Bit ##
# wget http://download.fedoraproject.org/pub/epel/6/i386/epel-release-6-8.noarch.rpm
# rpm -ivh epel-release-6-8.noarch.rpm
## RHEL/CentOS 6 64-Bit ##
# wget http://download.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm
# rpm -ivh epel-release-6-8.noarch.rpm
yum install s3cmd
For manual installation Download the tar file from
http://sourceforge.net/projects/s3tools/files/s3cmd/
get the tar file of the needed version .
make sure you have a python version > than 2.4 installed in the server.
untar the file using tar zxvf or zjvf as per the need and use python to run the installation script
python setup.py install
..
Configuring/Reconfiguring the s3cmd command
s3cmd --configure
Enter new values or accept defaults in brackets with Enter.
Refer to user manual for detailed description of all options.
Access key and Secret key are your identifiers for Amazon S3
Access Key: xxxxxxxxxxxxxxxxxxxxxx
Secret Key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Encryption password is used to protect your files from reading
by unauthorized persons while in transfer to S3
Encryption password: xxxxxxxxxx
Path to GPG program [/usr/bin/gpg]:
When using secure HTTPS protocol all communication with Amazon S3
servers is protected from 3rd party eavesdropping. This method is
slower than plain HTTP and can't be used if you're behind a proxy
Use HTTPS protocol [No]: Yes
New settings:
Access Key: xxxxxxxxxxxxxxxxxxxxxx
Secret Key: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
Encryption password: xxxxxxxxxx
Path to GPG program: /usr/bin/gpg
Use HTTPS protocol: True
HTTP Proxy server name:
HTTP Proxy server port: 0
Test access with supplied credentials? [Y/n] Y
Please wait, attempting to list all buckets...
Success. Your access key and secret key worked fine :-)
Now verifying that encryption works...
Success. Encryption and decryption worked fine :-)
Save settings? [y/N] y
Configuration saved to '/root/.s3cfg'
# s3cmd mb s3://test
Bucket 's3://test/' created
# s3cmd ls s3://test/
Upload a file
# s3cmd put file.txt s3://test/
Upload Similar files
# s3cmd put *.txt s3://test/
Uploading complete Directory
# s3cmd put -r upload-dir s3://test/
Upload files in a directory
# s3cmd put -r upload-dir/ s3://test/
Get a file
# s3cmd get s3://test/file.txt
Removing file from s3 bucket
# s3cmd del s3://test/file.txt
File s3://test/file.txt deleted
Removing directory from s3 bucket
# s3cmd del s3://test/backup
File s3://test/backup deleted
Sync direcotry .
# s3cmd sync ./back s3://test/back
attributes that can be used with Sync
--delete-removed :-remove files that are removed from the local directory .
--skip-existing :-Don't sync the files already synced.
—exclude / —include — standard shell-style wildcards, enclose them into apostrophes to avoid their expansion by the shell. For example --exclude 'x*.jpg' will match x12345.jpg but not abcdef.jpg.
—rexclude / —rinclude — regular expression version of the above. Much more powerful way to create match patterns. I realise most users have no clue about RegExps, which is sad. Anyway, if you’re one of them and can get by with shell style wildcards just use —exclude/—include and don’t worry about —rexclude/—rinclude. Or read some tutorial on RegExps, such a knowledge will come handy one day, I promise ;-)
—exclude-from / —rexclude-from / —(r)include-from — Instead of having to supply all the patterns on the command line, write them into a file and pass that file’s name as a parameter to one of these options. For instance --exclude '*.jpg' --exclude '*.gif' is the same as --
Wednesday, April 30, 2014
Tuesday, April 29, 2014
SSH-Tunneling
Main Options we use in ssh tunneling
-L [bind_address:]port:host:hostport
Specifies that the given port on the local (client) host is to be forwarded to the given host and port on the remote side. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and a connection is made to host port hostport from the remote machine. Port forwardings can also be specified in the configuration file. IPv6 addresses can be specified with an alternative syntax: [bind_address/]port/host/hostport or by enclosing the address in square brackets. Only the superuser can forward privileged ports. By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of “localhost” indicates that the listen- ing port be bound for local use only, while an empty address or ‘*’ indicates that the port should be available from all interfaces.
-f Requests ssh to go to background just before command execution.
This is use-ful if ssh is going to ask for passwords or passphrases, but the user wants it in the background. This implies -n. The recommended way to start X11 programs at a remote site is with something like ssh -f host xterm.
If the ExitOnForwardFailure configuration option is set to “yes”, then a client started with -f will wait for all remote port forwards to be success- fully established before placing itself in the background.
Difference between Reverse tunneling and Normal tunneling.
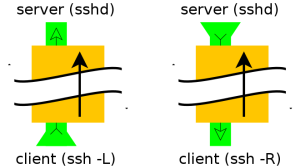
Normal tunneling
ssh -L 8888:www.linux.ro:80 user@computer -N
ssh -L 8888:www.linux.ro:80 -L 110:mail.linux.ro:110 \
25:mail.linux.ro:25 user@computer -N
The second example (see above) show you how to setup your ssh tunnel for web, pop3
and smtp. It is useful to recive/send your e-mails when you don't have direct access
to the mail server.
For the ASCII art and lynx browser fans here is illustrated the first example:
+--------------+<--port 22-->+--------------------+<--port 80-->o-----------+
|SSH Client|----------------------|ssh_server|----------------------| host |
+-------------------+ +----------+ o-----------+
localhost:8888 computer www.linuxon.ro:80
For example, if the remote server in question was myserver.example.com you could run the following command on your local system to create a tunnel as described above:
ssh -T -N -L 3308:localhost:3306 myserver.example.com
The meat of the command is the -L option, which tells ssh to listen on port 3308 locally and then on the remote side to forward all traffic on that port to localhost:3306. Note that the localhost here is not referring to the local system but rather where to forward things to on the remote side, in this case to localhost on the remote side.
ssh -T -N -L 3308:private.local:3306 myserver.example.com
Here, ssh listens on port 3308 on the local system and it forwards that data to port 3306 on private.host, but it does that via the server myserver.example.com. In other words the local traffic on port 3308 gets transferred first to the remote system which then transfers it to port 3306 on private.host. Of course, if private.local's mysql server is only listening on its local interface this won't work, you'll need something more involved.
ssh -R 9001:intra-site.com:80 home (Executed from 'work')
Once executed the SSH client at ‘work’ will connect to SSH server running at home creating a SSH channel. Then the server will bind port 9001 on ‘home’ machine to listen for incoming requests which would subsequently be routed through the created SSH channel between ‘home’ and ‘work’. Now it’s possible to browse the internal site
by visiting http://localhost:9001 in ‘home’ web browser. The ‘work’ will then create a connection to intra-site and relay back the response to ‘home’ via the created SSH channel.
-L [bind_address:]port:host:hostport
Specifies that the given port on the local (client) host is to be forwarded to the given host and port on the remote side. This works by allocating a socket to listen to port on the local side, optionally bound to the specified bind_address. Whenever a connection is made to this port, the connection is forwarded over the secure channel, and a connection is made to host port hostport from the remote machine. Port forwardings can also be specified in the configuration file. IPv6 addresses can be specified with an alternative syntax: [bind_address/]port/host/hostport or by enclosing the address in square brackets. Only the superuser can forward privileged ports. By default, the local port is bound in accordance with the GatewayPorts setting. However, an explicit bind_address may be used to bind the connection to a specific address. The bind_address of “localhost” indicates that the listen- ing port be bound for local use only, while an empty address or ‘*’ indicates that the port should be available from all interfaces.
-N Do not execute a remote command. This is useful for just forwarding ports (protocol version 2 only).
-R [bind_address:]port:host:hostport
Specifies that the given port on the remote (server) host is to be forwarded to the given host and port on the local side. This works by allocating a socket to listen to port on the remote side, and whenever a connection is made to this port, the connection is forwarded over the secure channel, and a connection is made to host port hostport from the local machine.
Specifies that the given port on the remote (server) host is to be forwarded to the given host and port on the local side. This works by allocating a socket to listen to port on the remote side, and whenever a connection is made to this port, the connection is forwarded over the secure channel, and a connection is made to host port hostport from the local machine.
Port forwardings can also be specified in the configuration file. Privileged ports can be forwarded only when logging in as root on the remote machine. IPv6 addresses can be specified by enclosing the address in square braces or using an alternative syntax: [bind_address/]host/port/hostport.
By default, the listening socket on the server will be bound to the loopback interface only. This may be overridden by specifying a bind_address. An empty bind_address, or the address ‘*’, indicates that the remote socket should listen on all interfaces. Specifying a remote bind_address will only succeed if the server’s GatewayPorts option is enabled (see sshd_config(5)).
If the port argument is ‘0’, the listen port will be dynamically allocated on the server and reported to the client at run time.
By default, the listening socket on the server will be bound to the loopback interface only. This may be overridden by specifying a bind_address. An empty bind_address, or the address ‘*’, indicates that the remote socket should listen on all interfaces. Specifying a remote bind_address will only succeed if the server’s GatewayPorts option is enabled (see sshd_config(5)).
If the port argument is ‘0’, the listen port will be dynamically allocated on the server and reported to the client at run time.
-f Requests ssh to go to background just before command execution.
This is use-ful if ssh is going to ask for passwords or passphrases, but the user wants it in the background. This implies -n. The recommended way to start X11 programs at a remote site is with something like ssh -f host xterm.
If the ExitOnForwardFailure configuration option is set to “yes”, then a client started with -f will wait for all remote port forwards to be success- fully established before placing itself in the background.
Difference between Reverse tunneling and Normal tunneling.

Normal tunneling
ssh -L 8888:www.linux.ro:80 user@computer -N
ssh -L 8888:www.linux.ro:80 -L 110:mail.linux.ro:110 \
25:mail.linux.ro:25 user@computer -N
The second example (see above) show you how to setup your ssh tunnel for web, pop3
and smtp. It is useful to recive/send your e-mails when you don't have direct access
to the mail server.
For the ASCII art and lynx browser fans here is illustrated the first example:
+--------------+<--port 22-->+--------------------+<--port 80-->o-----------+
|SSH Client|----------------------|ssh_server|----------------------| host |
+-------------------+ +----------+ o-----------+
localhost:8888 computer www.linuxon.ro:80
For example, if the remote server in question was myserver.example.com you could run the following command on your local system to create a tunnel as described above:
ssh -T -N -L 3308:localhost:3306 myserver.example.com
The meat of the command is the -L option, which tells ssh to listen on port 3308 locally and then on the remote side to forward all traffic on that port to localhost:3306. Note that the localhost here is not referring to the local system but rather where to forward things to on the remote side, in this case to localhost on the remote side.
ssh -T -N -L 3308:private.local:3306 myserver.example.com
Here, ssh listens on port 3308 on the local system and it forwards that data to port 3306 on private.host, but it does that via the server myserver.example.com. In other words the local traffic on port 3308 gets transferred first to the remote system which then transfers it to port 3306 on private.host. Of course, if private.local's mysql server is only listening on its local interface this won't work, you'll need something more involved.
ssh -R 9001:intra-site.com:80 home (Executed from 'work')
Once executed the SSH client at ‘work’ will connect to SSH server running at home creating a SSH channel. Then the server will bind port 9001 on ‘home’ machine to listen for incoming requests which would subsequently be routed through the created SSH channel between ‘home’ and ‘work’. Now it’s possible to browse the internal site
by visiting http://localhost:9001 in ‘home’ web browser. The ‘work’ will then create a connection to intra-site and relay back the response to ‘home’ via the created SSH channel.
Monday, April 28, 2014
SVN access manager
To use SVN Access Manager you need at least:
a working subversion installation
a MySQL Database, version 4 or higher, a PostgreSQL 8 or higher database or an Oracle 10g or higher database
an Apache web server, version 2.0 or higher with DAV, mod_authz and SVN support
PHP version 5.2 or higher with working oci8 support if using Oracle database
To use SVN Access Manager you need at least:
a working subversion installation
a MySQL Database, version 4 or higher, a PostgreSQL 8 or higher database or an Oracle 10g or higher database
an Apache web server, version 2.0 or higher with DAV, mod_authz and SVN support
PHP version 5.2 or higher with working oci8 support if using Oracle database
Go to a directory where the software can be accessed by your Apache web server. Unpack the archive. For our example do the following:
http://sourceforge.net/projects/svn-access-mana/files/
# mkdir /etc/svn
# mkdir /etc/svn-access-manager
# mkdir /usr/share/svn-access-manager
# chown apache:apache /etc/svn /etc/svn-access-manager
# cd /usr/share/svn-access-manager
# tar -xvfz svnaccessmanager-0.5.0.0.tar.gz
2.2.3 Setup a MySQL database and a database user
You need a database for SVN Access Manager and an user with full access to this database. To create the database do the following as root user of your MySQL database:
CREATE DATABASE svnadmin;
To create a user having access to this database do the following as root user of your MySQL database:
CREATE USER 'svnadmin'@ 'localhost' IDENTIFIED BY '*******';
GRANT USAGE ON * . * TO 'svnadmin'@ 'localhost' IDENTIFIED BY '*******'
WITH MAX_QUERIES_PER_HOUR 0 MAX_CONNECTIONS_PER_HOUR 0
MAX_UPDATES_PER_HOUR 0 MAX_USER_CONNECTIONS 0 ;
GRANT ALL PRIVILEGES ON `svnadmin` . * TO 'svnadmin'@ 'localhost';
After finishing the database work continue with installing SVN Access Manager.
If you get an error "No database selected" during installation check if the database user has sufficient rights to access and to work with the database!
a working subversion installation
a MySQL Database, version 4 or higher, a PostgreSQL 8 or higher database or an Oracle 10g or higher database
an Apache web server, version 2.0 or higher with DAV, mod_authz and SVN support
PHP version 5.2 or higher with working oci8 support if using Oracle database
To use SVN Access Manager you need at least:
a working subversion installation
a MySQL Database, version 4 or higher, a PostgreSQL 8 or higher database or an Oracle 10g or higher database
an Apache web server, version 2.0 or higher with DAV, mod_authz and SVN support
PHP version 5.2 or higher with working oci8 support if using Oracle database
Go to a directory where the software can be accessed by your Apache web server. Unpack the archive. For our example do the following:
http://sourceforge.net/projects/svn-access-mana/files/
# mkdir /etc/svn
# mkdir /etc/svn-access-manager
# mkdir /usr/share/svn-access-manager
# chown apache:apache /etc/svn /etc/svn-access-manager
# cd /usr/share/svn-access-manager
# tar -xvfz svnaccessmanager-0.5.0.0.tar.gz
2.2.3 Setup a MySQL database and a database user
You need a database for SVN Access Manager and an user with full access to this database. To create the database do the following as root user of your MySQL database:
CREATE DATABASE svnadmin;
To create a user having access to this database do the following as root user of your MySQL database:
CREATE USER 'svnadmin'@ 'localhost' IDENTIFIED BY '*******';
GRANT USAGE ON * . * TO 'svnadmin'@ 'localhost' IDENTIFIED BY '*******'
WITH MAX_QUERIES_PER_HOUR 0 MAX_CONNECTIONS_PER_HOUR 0
MAX_UPDATES_PER_HOUR 0 MAX_USER_CONNECTIONS 0 ;
GRANT ALL PRIVILEGES ON `svnadmin` . * TO 'svnadmin'@ 'localhost';
After finishing the database work continue with installing SVN Access Manager.
If you get an error "No database selected" during installation check if the database user has sufficient rights to access and to work with the database!
SVN-Subversion installation and configuration
Installing SVN
yum install mod_dav_svn subversion
Add it in httpd conf or in httpd/conf.d/subversion.conf
LoadModule dav_svn_module modules/mod_dav_svn.so
LoadModule authz_svn_module modules/mod_authz_svn.so
<Location /svn>
DAV svn
SVNParentPath /var/www/svn
AuthType Basic
AuthName "Subversion repositories"
AuthUserFile /etc/svn-auth-users
Require valid-user
</Location>
Creating User for accessing the SVN
htpasswd -cm /etc/svn-auth-users user1
New password:
Re-type new password:
Adding password for user user1
## Create user2 ##
htpasswd -m /etc/svn-auth-users user2
New password:
Re-type new password:
Adding password for user user2
Creating the directories and correcting permissions
mkdir /var/www/svn
cd /var/www/svn
Creating repositories
svnadmin create testrepo
chown -R apache.apache testrepo
## If you have SELinux enabled (you can check it with "sestatus" command) ##
## then change SELinux security context with chcon command ##
chcon -R -t httpd_sys_content_t /var/www/svn/testrepo
## Following enables commits over http ##
chcon -R -t httpd_sys_rw_content_t /var/www/svn/testrepo
or else disable the selinux
setenforce 0
Restart the service
systemctl restart httpd.service
## OR ##
service httpd restart
## CentOS / RHEL ##
/etc/init.d/httpd restart
## OR ##
service httpd restart
Friday, April 25, 2014
Linux Acl in detail
Let's assume we have /dev/sda1 mounted on /data1 and we want to enable the acl option.
[root@server ~]# tune2fs -l /dev/sda1
To enable ACLs on a filesystem, we must set the fs default and remount:
[root@server ~]# tune2fs -o acl /dev/sda1
[root@server ~]# mount -o remount,acl /data1
Use getfacl to view ACLs:
[root@server ~]# touch /data1/foo.txt
[root@server ~]# getfacl /data1/foo.txt
getfacl: Removing leading '/' from absolute path names
# file: data1/foo.txt
# owner: root
# group: root
user::rw-
group::r--
other::r--
Use setfacl to set ACLs, with -m to modify and -x to remove a given ACL.
give user ram read+write+execute on a file:
[root@server ~]# setfacl -m u:ram:rwx /data1/foo.txt
give group peeps read+write on a file:
[root@server ~]# setfacl -m g:peeps:rw /data1/foo.txt
remove ram's ACL permissions:
[root@server ~]# setfacl -x u:ram /data1/foo.txt
set the default ACL permissions on a directory:
[root@server ~]# setfacl -m d:g:peeps:rw /data1/stuff/
revoke write permission for everyone:
[root@server ~]# setfacl -m m::rx /data1/foo.txt
When ACLs are present, an ls -l will show a plus sign to notify you:
[root@server ~]# ls -l /data1/foo.txt
-rw-rwxr--+ 1 root root 0 Dec 3 14:54 /data1/foo.txt
Note that the mv and cp -p commands will preserve ACLs. If you have defaults set on a parent directory, new files in that directory will inherit those settings.
If you want to remove all ACLs, reverting back to the base unix permissions of owner, group and other:
[root@server ~]# setfacl --remove-all /data1/foo.txt
[root@server ~]# tune2fs -l /dev/sda1
To enable ACLs on a filesystem, we must set the fs default and remount:
[root@server ~]# tune2fs -o acl /dev/sda1
[root@server ~]# mount -o remount,acl /data1
Use getfacl to view ACLs:
[root@server ~]# touch /data1/foo.txt
[root@server ~]# getfacl /data1/foo.txt
getfacl: Removing leading '/' from absolute path names
# file: data1/foo.txt
# owner: root
# group: root
user::rw-
group::r--
other::r--
Use setfacl to set ACLs, with -m to modify and -x to remove a given ACL.
give user ram read+write+execute on a file:
[root@server ~]# setfacl -m u:ram:rwx /data1/foo.txt
give group peeps read+write on a file:
[root@server ~]# setfacl -m g:peeps:rw /data1/foo.txt
remove ram's ACL permissions:
[root@server ~]# setfacl -x u:ram /data1/foo.txt
set the default ACL permissions on a directory:
[root@server ~]# setfacl -m d:g:peeps:rw /data1/stuff/
revoke write permission for everyone:
[root@server ~]# setfacl -m m::rx /data1/foo.txt
When ACLs are present, an ls -l will show a plus sign to notify you:
[root@server ~]# ls -l /data1/foo.txt
-rw-rwxr--+ 1 root root 0 Dec 3 14:54 /data1/foo.txt
Note that the mv and cp -p commands will preserve ACLs. If you have defaults set on a parent directory, new files in that directory will inherit those settings.
If you want to remove all ACLs, reverting back to the base unix permissions of owner, group and other:
[root@server ~]# setfacl --remove-all /data1/foo.txt
Thursday, April 24, 2014
Flush Your Local DNS Cache
Windows Vista/Windows 7:
ipconfig /flushdns
Successfully flushed the DNS Resolver Cache.
Windows XP
ipconfig /flushdns
Successfully flushed the DNS Resolver Cache.
Mac OS X 10.5.2 and above
dscacheutil -flushcache
Mac OS X 10.5.1 and below
Click on the Finder icon in your dock. Open your Applications folder.
Inside the Applications folder, click on Utilities and then Terminal.
Type the following command in the Terminal window and press Enter:
lookupd -flushcache
Linux
nscd -i hosts
– Clear local DNS cache for current user.
nscd -I hosts
– Clear local DNS cache for all users.
Wednesday, April 23, 2014
Creating a custom Nagios function
Nagios Exit Codes
Exit Code Status
0 OK
1 WARNING
2 CRITICAL
3 UNKNOWN
Create the Script to be added as the Plugin
#!/bin/bash
used_space=`df -h / | grep -v Filesy | awk '{print $5}' | sed 's/%//g'`
case $used_space in
[1-84]*)
echo "OK - $used_space% of disk space used."
exit 0
;;
[85]*)
echo "WARNING - $used_space% of disk space used."
exit 1
;;
[86-100]*)
echo "CRITICAL - $used_space% of disk space used."
exit 2
;;
*)
echo "UNKNOWN - $used_space% of disk space used."
exit 3
;;
esac
try to put the script in same plugin directory with the other ones
/usr/lib/nagios/plugins/
make it executable
Add Your New Command to Nagios Checks on Nagios Monitoring Server
Define new command in /etc/nagios/objects/commands.cfg
define command{
command_name usedspace_bash
command_line $USER1$/check_nrpe -H $HOSTADDRESS$ -c usedspace_bash
}
Add Your Script to NRPE configuration on client host
command[usedspace_bash]=/usr/lib/nagios/plugins/usedspace.sh
adding to configuration
/etc/nagios/servers/<name-0f-config>.cfg
define service {
use generic-service
host_name Hostname
service_description Custom Disk Checker In Bash
check_command usedspace_bash
}
Exit Code Status
0 OK
1 WARNING
2 CRITICAL
3 UNKNOWN
Create the Script to be added as the Plugin
#!/bin/bash
used_space=`df -h / | grep -v Filesy | awk '{print $5}' | sed 's/%//g'`
case $used_space in
[1-84]*)
echo "OK - $used_space% of disk space used."
exit 0
;;
[85]*)
echo "WARNING - $used_space% of disk space used."
exit 1
;;
[86-100]*)
echo "CRITICAL - $used_space% of disk space used."
exit 2
;;
*)
echo "UNKNOWN - $used_space% of disk space used."
exit 3
;;
esac
try to put the script in same plugin directory with the other ones
/usr/lib/nagios/plugins/
make it executable
Add Your New Command to Nagios Checks on Nagios Monitoring Server
Define new command in /etc/nagios/objects/commands.cfg
define command{
command_name usedspace_bash
command_line $USER1$/check_nrpe -H $HOSTADDRESS$ -c usedspace_bash
}
Add Your Script to NRPE configuration on client host
command[usedspace_bash]=/usr/lib/nagios/plugins/usedspace.sh
adding to configuration
/etc/nagios/servers/<name-0f-config>.cfg
define service {
use generic-service
host_name Hostname
service_description Custom Disk Checker In Bash
check_command usedspace_bash
}
Tuesday, April 22, 2014
Adding ESXI to Nagios
yum install perl-Pod-Perldoc perl-CPAN openssl-devel
# wget http://dl.fedoraproject.org/pub/epel/6/i386/perl-Nagios-Plugin-0.35-1.el6.noarch.rpm
# wget http://mirror.centos.org/centos/6/os/i386/Packages/perl-Config-Tiny-2.12-7.1.el6.noarch.rpm
# wget http://mirror.centos.org/centos/6/os/i386/Packages/perl-Params-Validate-0.92-3.el6.i686.rpm
# rpm -ivh perl-Nagios-Plugin-0.35-1.el6.noarch.rpm perl-Config-Tiny-2.12-7.1.el6.noarch.rpm perl-Params-Validate-0.92-3.el6.i686.rpm
# cd /root
# tar xvzf VMware-vSphere-Perl-SDK-4.1.0-254719.i386.tar.gz
# cd vmware-vsphere-cli-distrib/
# ./vmware-install.pl
# cd /usr/lib/nagios/plugins/
Download check_esx3.pl and make it executable
http://exchange.nagios.org/components/com_mtree/attachment.php?link_id=2154&cf_id=29
chmod +x check_esx3.pl
vim /usr/local/nagios/etc/objects/vmware.cfg
First define all your hosts as shown below
# Host esx01
define host{
use vmware-server
host_name esxi01
alias VMWare ESXi 01
address IP Address
}
define host{
use vmware-server
host_name esxi02
alias VMWare ESXi 02
address IP Address
}
# Similarly you can define all the hosts
# Now define a hostgroup for your Esxi Hosts:
define hostgroup{
hostgroup_name Esxi-Servers ; The name of the hostgroup
alias Vmware Servers ; Long name of the group
members esxi01,esxi02
}
# Now create the service definition as shown below
# check cpu
define service{
use generic-service
host_name esxi01
service_description ESXi CPU Load
check_command check_esx_cpu!80!90
}
# check memory usage
define service{
use generic-service
host_name esxi01
service_description ESXi Memory usage
check_command check_esx_mem!80!90
}
# check net
define service{
use generic-service
host_name esxi01
service_description ESXi Network usage
check_command check_esx_net!102400!204800
}
# check runtime status
define service{
use generic-service
host_name esxi01
service_description ESXi Runtime status
check_command check_esx_runtime
}
# check io read
define service{
use generic-service
host_name esxi01
service_description ESXi IO read
check_command check_esx_ioread!40!90
}
# check io write
define service{
use generic-service
host_name esxi01
service_description ESXi IO write
check_command check_esx_iowrite!40!90
}
Define the commands related to ESXi in the /usr/local/nagios/etc/objects/command.cfg file
vim /usr/local/nagios/etc/objects/commands.cfg
# check vmware esxi machine
# check cpu
define command{
command_name check_esx_cpu
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l cpu -s usage -w $ARG1$ -c $ARG2$
}
# check memory usage
define command{
command_name check_esx_mem
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l mem -s usage -w $ARG1$ -c $ARG2$
}
# check net usage
define command{
command_name check_esx_net
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l net -s usage -w $ARG1$ -c $ARG2$
}
# check runtime status
define command{
command_name check_esx_runtime
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l runtime -s status
}
# check io read
define command{
command_name check_esx_ioread
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l io -s read -w $ARG1$ -c $ARG2$
}
# check io write
define command{
command_name check_esx_iowrite
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l io -s write -w $ARG1$ -c $ARG2$
}
Adding configuration to nagios
vim /usr/local/nagios/etc/nagios.cfg
cfg_file=/usr/local/nagios/etc/objects/vmware.cfg
# wget http://dl.fedoraproject.org/pub/epel/6/i386/perl-Nagios-Plugin-0.35-1.el6.noarch.rpm
# wget http://mirror.centos.org/centos/6/os/i386/Packages/perl-Config-Tiny-2.12-7.1.el6.noarch.rpm
# wget http://mirror.centos.org/centos/6/os/i386/Packages/perl-Params-Validate-0.92-3.el6.i686.rpm
# rpm -ivh perl-Nagios-Plugin-0.35-1.el6.noarch.rpm perl-Config-Tiny-2.12-7.1.el6.noarch.rpm perl-Params-Validate-0.92-3.el6.i686.rpm
# cd /root
# tar xvzf VMware-vSphere-Perl-SDK-4.1.0-254719.i386.tar.gz
# cd vmware-vsphere-cli-distrib/
# ./vmware-install.pl
# cd /usr/lib/nagios/plugins/
Download check_esx3.pl and make it executable
http://exchange.nagios.org/components/com_mtree/attachment.php?link_id=2154&cf_id=29
chmod +x check_esx3.pl
vim /usr/local/nagios/etc/objects/vmware.cfg
First define all your hosts as shown below
# Host esx01
define host{
use vmware-server
host_name esxi01
alias VMWare ESXi 01
address IP Address
}
define host{
use vmware-server
host_name esxi02
alias VMWare ESXi 02
address IP Address
}
# Similarly you can define all the hosts
# Now define a hostgroup for your Esxi Hosts:
define hostgroup{
hostgroup_name Esxi-Servers ; The name of the hostgroup
alias Vmware Servers ; Long name of the group
members esxi01,esxi02
}
# Now create the service definition as shown below
# check cpu
define service{
use generic-service
host_name esxi01
service_description ESXi CPU Load
check_command check_esx_cpu!80!90
}
# check memory usage
define service{
use generic-service
host_name esxi01
service_description ESXi Memory usage
check_command check_esx_mem!80!90
}
# check net
define service{
use generic-service
host_name esxi01
service_description ESXi Network usage
check_command check_esx_net!102400!204800
}
# check runtime status
define service{
use generic-service
host_name esxi01
service_description ESXi Runtime status
check_command check_esx_runtime
}
# check io read
define service{
use generic-service
host_name esxi01
service_description ESXi IO read
check_command check_esx_ioread!40!90
}
# check io write
define service{
use generic-service
host_name esxi01
service_description ESXi IO write
check_command check_esx_iowrite!40!90
}
Define the commands related to ESXi in the /usr/local/nagios/etc/objects/command.cfg file
vim /usr/local/nagios/etc/objects/commands.cfg
# check vmware esxi machine
# check cpu
define command{
command_name check_esx_cpu
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l cpu -s usage -w $ARG1$ -c $ARG2$
}
# check memory usage
define command{
command_name check_esx_mem
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l mem -s usage -w $ARG1$ -c $ARG2$
}
# check net usage
define command{
command_name check_esx_net
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l net -s usage -w $ARG1$ -c $ARG2$
}
# check runtime status
define command{
command_name check_esx_runtime
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l runtime -s status
}
# check io read
define command{
command_name check_esx_ioread
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l io -s read -w $ARG1$ -c $ARG2$
}
# check io write
define command{
command_name check_esx_iowrite
command_line $USER1$/check_esx -H $HOSTADDRESS$ -u $USER11$ -p $USER12$ -l io -s write -w $ARG1$ -c $ARG2$
}
Adding configuration to nagios
vim /usr/local/nagios/etc/nagios.cfg
cfg_file=/usr/local/nagios/etc/objects/vmware.cfg
Tuesday, April 15, 2014
Openssl-heartbleed-fix
Downloading and updating the SSL.
cd /usr/src
wget http://www.openssl.org/source/openssl-1.0.1g.tar.gz
tar -zxf openssl-1.0.1g.tar.gz
cd openssl-1.0.1g
./config shared
make
make test
make install
cd /usr/src
rm -rf openssl-1.0.1g.tar.gz
rm -rf openssl-1.0.1g
to over write the current open ssl use the following config mode .
./config --prefix=/usr --openssldir=/usr/local/openssl shared Sunday, April 13, 2014
Ubuntu- DNS - setting it to static and dynamic
In case of static
cat /etc/network/interfaces
cat /etc/network/interfaces
# The loopback network interfaceSetting it to dhcp
auto lo
iface lo inet loopback
# The primary network interface
auto eth0
iface eth0 inet static
address 192.168.1.58
gateway 192.168.1.1
network 192.168.1.0
broadcast 192.168.1.255
dns-nameservers 66.212.63.228 66.212.48.10
iface eth0 inet dhcp
Friday, April 11, 2014
Mod-Security Installing Along with - Open Source Rules
Installing the Mod Security.
## For RHEL/CentOS 6.2/6.1/6/5.8 ##
Installing needed Modules
yum install gcc make
yum install libxml2 libxml2-devel httpd-devel pcre-devel curl-devel\
Installing the Mod-Security
## For RHEL/CentOS 6.2/6.1/6/5.8 ##
cd /usr/src
wget http://www.modsecurity.org/download/modsecurity-apache_2.6.6.tar.gz
tar xzf modsecurity-apache_2.6.6.tar.gz
cd modsecurity-apache_2.6.6
./configure
make install
cp modsecurity.conf-recommended /etc/httpd/conf.d/modsecurity.conf
Adding the Mod-security Module to the Apache
# vi /etc/httpd/conf/httpd.conf
LoadModule unique_id_module modules/mod_unique_id.so
LoadModule security2_module modules/mod_security2.so
[root@54 modsecurity-apache_2.6.6]# httpd -t -D DUMP_MODULES |grep sec
security2_module (shared)
Syntax OK
[root@54 modsecurity-apache_2.6.6]#
<IfModule security2_module>
Include conf.d/modsecurity.conf
</IfModule>
Adding new Mod-Security Rules ..
OWASP core rule set
wget http://pkgs.fedoraproject.org/repo/pkgs/mod_security_crs/modsecurity-crs_2.2.5.tar.gz/a
aeaa1124e8efc39eeb064fb47cfc0aa/modsecurity-crs_2.2.5.tar.gz
tar zxvf modsecurity-crs_2.2.5.tar.gz
mv modsecurity-crs_2.2.5 modsecurity-crs
mv modsecurity-crs /etc/httpd/conf.d/
Adding the rules to httpd
<IfModule security2_module>
Include conf.d/modsecurity.conf
Include conf.d/modsecurity-crs/activated_rules/*.conf
Include conf.d/modsecurity-crs/base_rules/*.conf
Include conf.d/modsecurity-crs/optional_rules/*.conf
Include conf.d/modsecurity-crs/slr_rules/*.conf
</IfModule>
More rules are available at
## For RHEL/CentOS 6.2/6.1/6/5.8 ##
Installing needed Modules
yum install gcc make
yum install libxml2 libxml2-devel httpd-devel pcre-devel curl-devel\
Installing the Mod-Security
## For RHEL/CentOS 6.2/6.1/6/5.8 ##
cd /usr/src
wget http://www.modsecurity.org/download/modsecurity-apache_2.6.6.tar.gz
tar xzf modsecurity-apache_2.6.6.tar.gz
cd modsecurity-apache_2.6.6
./configure
make install
cp modsecurity.conf-recommended /etc/httpd/conf.d/modsecurity.conf
Adding the Mod-security Module to the Apache
# vi /etc/httpd/conf/httpd.conf
LoadModule unique_id_module modules/mod_unique_id.so
LoadModule security2_module modules/mod_security2.so
[root@54 modsecurity-apache_2.6.6]# httpd -t -D DUMP_MODULES |grep sec
security2_module (shared)
Syntax OK
[root@54 modsecurity-apache_2.6.6]#
<IfModule security2_module>
Include conf.d/modsecurity.conf
</IfModule>
Adding new Mod-Security Rules ..
OWASP core rule set
wget http://pkgs.fedoraproject.org/repo/pkgs/mod_security_crs/modsecurity-crs_2.2.5.tar.gz/a
aeaa1124e8efc39eeb064fb47cfc0aa/modsecurity-crs_2.2.5.tar.gz
tar zxvf modsecurity-crs_2.2.5.tar.gz
mv modsecurity-crs_2.2.5 modsecurity-crs
mv modsecurity-crs /etc/httpd/conf.d/
Adding the rules to httpd
<IfModule security2_module>
Include conf.d/modsecurity.conf
Include conf.d/modsecurity-crs/activated_rules/*.conf
Include conf.d/modsecurity-crs/base_rules/*.conf
Include conf.d/modsecurity-crs/optional_rules/*.conf
Include conf.d/modsecurity-crs/slr_rules/*.conf
</IfModule>
More rules are available at
sudo wget -O SpiderLabs-owasp-modsecurity-crs.tar.gz https://github.com/SpiderLabs/owasp-modsecurity-crs/tarball/master
Now the Mod Security is in the detect mode . once we are set we need to move it to on mode
[root@54 conf]# cat /etc/httpd/conf.d/modsecurity.conf |grep SecRuleEngine -i
SecRuleEngine DetectionOnly
# when SecRuleEngine is set to DetectionOnly mode in order to minimize
[root@54 conf]#
Change to
SecRuleEngine on
Thursday, April 10, 2014
Setting the Mysql into a ReadOnly mode..
whole database to read only mode by this commands:
In the MySQL Prompt
FLUSH TABLES WITH READ LOCK;
SET GLOBAL read_only = 1;
and back to normal mode with:
SET GLOBAL read_only = 0;
UNLOCK TABLES;
In the MySQL Prompt
FLUSH TABLES WITH READ LOCK;
SET GLOBAL read_only = 1;
and back to normal mode with:
SET GLOBAL read_only = 0;
UNLOCK TABLES;
Subscribe to:
Posts (Atom)