An AWS account has full permission to perform all actions on the vaults in the account. However, the AWS Identity and Access Management (IAM) users don't have any permission by default.
IAM helps us to securely control access to Amazon Web Services and your account resources. With IAM, you can create multiple IAM users under the umbrella of your AWS account.
Every user you create in the IAM system starts with no permissions. In other words, by default, users can do nothing. Permission is a general term we use to mean the ability to perform an action against a resource, unless you explicitly grant a user permissions, that user cannot perform any of these actions. You grant permission to a user with a policy. A policy is a document that formally states one or more permissions.
IAM Users
An IAM user is an entity that you create in AWS that provides a way to interact with AWS. A primary use for IAM users is to give people you work with identities that they can use to sign in to the AWS Management Console and to make requests to AWS services.
AWS IAM GROUP.
A
group is a collection of IAM users. Groups let you specify permissions for a collection of users, which can make it easier to manage the permissions for those users. For example, you could have a group called
Admins and give that group the types of permissions that administrators typically need. Any user in that group automatically has the permissions that are assigned to the group. If a new user joins your organization and should have administrator privileges, you can assign the appropriate permissions by adding the user to that group. Similarly, if a person changes jobs in your organization, instead of editing that user's permissions, you can remove him or her from the old group and add him or her to the new group.

Creating a Group with needed Privileges.
Entering the Group Name

Selecting Permissions
Aws provides a set of custom permission templates which we can use. The custom template provided by the Aws covers all the services in the AWS.
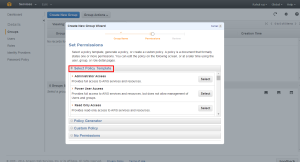
We can also generate Custom Policies with the help of Policy Generator

First select the service of which we need to create Policies.

Select the permission’s we need to add into the Policies
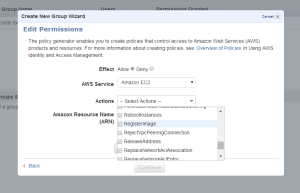
The Amazon Resource Name : This gives the API details about the service ,region, resource account ect.
Arn format
==========
arn:aws:service:region:account:resource
arn:aws:service:region:account:resourcetype/resource
arn:aws:service:region:account:resourcetype:resource
More details can be found at
http://docs.aws.amazon.com/general/latest/gr/aws-arns-and-namespaces.html

Once the ARN is added we can Add Statement so that we can see the rule’s added.

Now we will be able to see the policy codes which if needed we can use for create custom Policies.
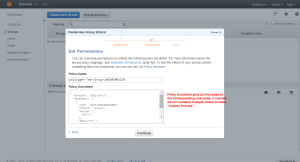
Creating the Group

Creating the User

Keep the Access Key ID and Secret Key safe because this is the last time you will see it in AWS. AWS will not save them for you. But you can create as many keys you need.

Adding the User to Group
Right click on the needed user to get more options.

Select the required Group

Once the group is added we need to give the user a password

Assign the needed Password
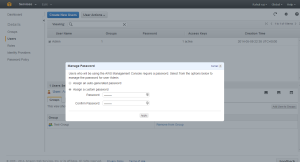
The Group and password are set for the User.
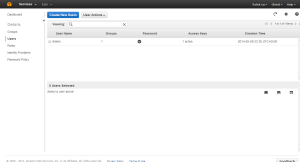
Once the User is set we can set the IAM URL alias

Give the needed Alias
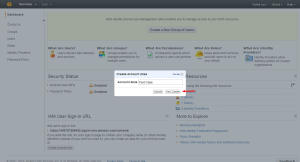
The URL is set.

Now you can use the URL to access the IAM login portal.



















